Wednesday, May 18, 2016
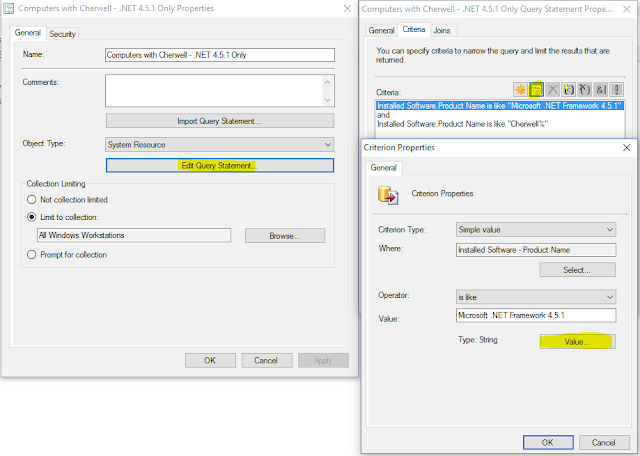
Expand Values in SCCM Query Builder Values Box
Friday, May 13, 2016
Step by Step Setup of MDT 2013 Update 2 Server
SCENARIO
You want a quick walk through on how to setup MDT 2013 Update 2 so that you can get started using it in your environment.
WHAT YOU WILL NEED
- A server OS - Server 2008 R2 or higher. We will be using Server 2012 R2 in this scenario.
- Windows Deployment Services role installed on our server.
- Download MDT 2013 Update 2. You can find it here.
- Download Windows ADK for Windows 10. You can find that here.
- Client OS (Win7, Win8, Win10) - whatever you plan on deploying.
- Drivers for the machines you are deploying to.
Driver Packs
Manufactures make driver packs for their various models. Use these!!!
HP WinPE Drivers - http://ftp.hp.com/pub/caps-softpaq/cmit/HP_WinPE_DriverPack.html
Lenovo Drivers - https://support.lenovo.com/cy/en/documents/ht074984
Tuesday, May 10, 2016
Break shared service into it's own process
SCENARIO: You are troubleshooting an issue and find that the problem is related to service that is shared. For example, say you identify a specific svchost process that is causing high CPU and you think you have identified one of the services running in that svchost as the culprit and you want to isolate it so that you can get a dump of that process. Here is a way to do that.
Friday, May 6, 2016
PowerShell Performance Diagnostics Utility
SCENARIO: You want to be able to create, start, stop, and delete Performance Monitor data collector sets and collect logs from your computer using a menu. You can do all of these things manually, but this script will present you with a menu for performing these tasks.
NOTE: This will work in Windows 10. If you are running on an older version of PowerShell, you will need to change Get-CimInstance cmdlet along with the Get-GPResultantSetOfPolicy cmdlet.
UPDATE: 11-06-2017 - I just pasted a newer version of this script below.
Click Here to Download Script: Data Collection Utility
Folder Structure:
Powershell Script: Copy files from multiple source directories
While you can create a package or application that copies config files out to
your clients after an install, there may be times when it's easier to just use
a PowerShell script to copy configuration files to your client machines.
This was true in our case where we had to copy files from different source
directories depending on the name of the computer. In our case, we had
to copy a different configuration file to C:\Program Files (x86)\application\
depending on which site that computer was at. Our computers have a four
digit site identifier at the beginning so we leveraged this in order to do the
file copy.
You can modify the script to accommodate your computer name scheme.
Force Mozilla Firefox to "Always Activate" Java
Scenario
You have installed the most recent version of Java, but when you check the Add-on Manager in Mozilla Firefox, you see that the Java Plugin defaults to "Ask to Activate". Typically you should probably leave it at "Ask to Activate" for security reasons, but if you want it to default to "Always Activate" you can do this either per user or per machine.Wednesday, April 6, 2016
Create Perfmon on Remote Machines
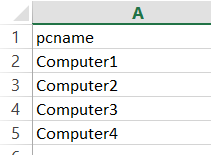
Scenario: You want to start perfmon on several remote machines. You have a list of machines, but you don't want to remotely create and start those perfmon data collector sets.
Here is a PowerShell script that you can use to start up perfmon data collector sets on a remote machine. It pulls the list of computers from a .csv file called "computers.csv". Your .csv should looks something like this:
Saturday, October 10, 2015
Highly Available 2008 R2 RDS Infrastructure
SCENARIO: Deploy highly available 2008 R2 Connection Broker. There are different ways to do this, but in our scenario, we will cluster the connection broker server, create a shared cluster service, and use NLB to balance the initial connection load on the session hosts.
PREREQUISITES:
SESSION HOSTS
2 Server 2008 R2 Servers with Session Host Roll installed
Session Host servers should have two NIC's (One for RDP and the other for NLB)
CONNECTION BROKERS
2 Server 2008 R2 servers with Connection Broker Roll installed.
Ensure that all servers are members of the same domain.
Ensure that all servers are able to communicate with each other (work out subnet / VLAN issues if any exist)
STEPS OVERVIEW
1. Install Failover Cluster feature on Connection Brokers
2. Create drive / folder for quorum drive (this is for failover clustering and in this example we will use a folder)
3. Create share cluster service.
4. Install NLB on Session Hosts.
5. Configure NLB on Session Hosts.
6. Create Session Host Farm.
7. Create appropriate DNS entries.
Saturday, June 27, 2015
Using Perfmon to Analyze High CPU Usage.
Scenario
Your CPU utilization is maxing out and you want to find how what is responsible for the high CPU. Sometimes the process is obvious in that you can look at task manager to see who is using the most CPU, but that alone doesn't give you a snapshot of what is happening on your server over a period of time.To begin, use the instructions from this article to capture perfmon data while you are experiencing the high CPU state. Let it capture a decent amount of time so that you can see trends.
After you capture the perfmon data, open it up by double clicking on the appropriate .blg file in the C:\Perflogs folder. You should see something like the above image. Unfortunately, this image isn't terribly helpful. So we will need to remove all the counters and then start by adding counters systematically.
Friday, June 26, 2015
Creating Secure Personal Drive Space
Scenario
Your job has given you a "work laptop" that you also use (legitimately, of course) for your own occasional personal computing, so you've amassed some personal files over the course of your employment. Now suppose that computer got taken away from you before you had a chance to get those files off? Perhaps one day you walk into your office and find a brand new laptop waiting for you. Cool! Except - where is your old one? "Don't worry!" says Helpful I.T. Guy, "All your work files are on the network, just log in to this new one and you'll have them." Yes, but were your personal files deleted? And if not, does the person who now has your old computer have access to those files?That's not an unlikely scenario - and worse ones can be imagined. What if one day your HR rep walks in with a security guard to announce that you've been downsized - "Stop what you're doing on that computer, gather your personal belongings, and come with us." Now what?
In this article I will explain my setup for avoiding issues like this. In reality the entire setup is fairly straightforward and not very time consuming, it actually took me several times longer to write the article than to do the setup! So don't be afraid to jump in.
Subscribe to:
Posts (Atom)